In mid-September, we reported that Nick Wellnhofer, the long-time maintainer of the widely used XML parsing library libxml2, planned to step down from the project. A few days ago, that change became official.
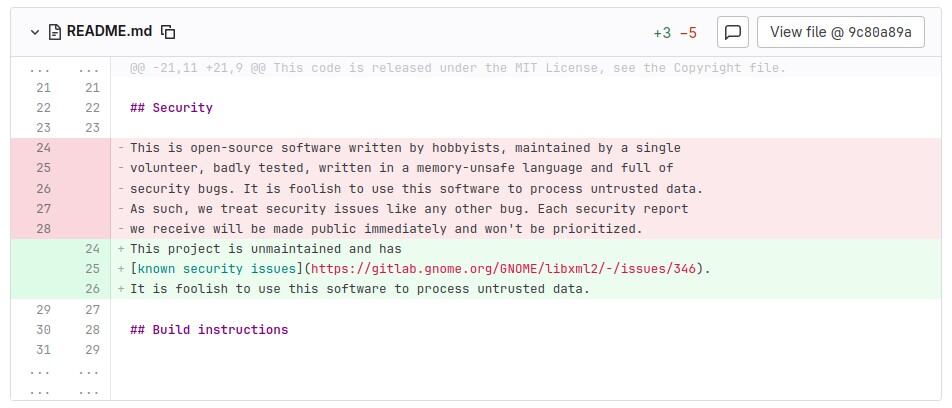
When looking at one of the latest commits in the project’s GitLab repository, you can now see the following notice:
“This project is unmaintained and has known security issues (https://gitlab.gnome.org/GNOME/libxml2/-/issues/346).
It is foolish to use this software to process untrusted data.”
And that’s very concerning news. Before you think, “So what, it’s just a library,” remember that we’re talking about a core piece of the Linux ecosystem, deeply embedded across infrastructure, desktop environments, programming languages, and security-sensitive workloads. Let me explain.
First, libxml2 is the de facto standard XML and HTML parsing library in the open-source world. It is pulled in by thousands of packages, from low-level system components to high-level applications. Almost all desktop environments depend heavily on it, as do major desktop tools, configuration systems, and document-processing pipelines.
Second, XML parsing is historically one of the most security-sensitive areas in systems programming. Vulnerabilities in XML libraries often lead to remote code execution, entity expansion attacks, information leakage, or denial-of-service issues.
And last but definitely not least, practically all Linux distros ship libxml2 as a core library. Just look at the packages on your system that depend on libxml2, and you’ll see a mile-long list you probably never even knew was there.
So, even a single unpatched security issue can force distributions to carry custom patches, maintain downstream forks, or replace the parser entirely. However, because libxml2 is deeply embedded in system libraries and applications, replacing it is practically impossible (or at least for the foreseeable future).
This is why libxml2 becoming unmaintained is not simply a minor upstream change. In fact, it represents a vulnerability point at the heart of the Linux and open-source infrastructure. Unless a new maintainer steps forward or the community organizes a coordinated fork, the risk will only increase.
All we can hope is that, before newly uncovered issues in the library begin to be exploited, it finds a new maintainer to carry on Wellnhofer’s excellent work, work he sustained for so many years and for which we owe him deep gratitude.

Mandatory xkcd 2347 reference