SSH is used for logging into servers to run the commands and programs remotely. However, sometimes you might want or even need to automatically log in to an SSH server without entering your username and password.
The two most popular mechanisms to log into remote systems via SSH are password-based authentication and key-based authentication.
Username and password combination is the most common authentication method for SSH and is suitable for most people. Unfortunately, there are certain security risks associated with using this method.
On the other hand, if you regularly use SSH to connect to remote servers, the key-based authentication method is best for you.
So, can you SSH without a password? In short, yes! Here’s how to do it.
Step 1: Generate SSH Key Pair
You first need to generate an SSH key pair on the machine you are currently working on.
If you are unsure how to do it I recommend following our short and easy to follow guide: Generate an SSH Key Pair [with Examples].
Step 2: Copy the Public Key to Remote Server
To enable SSH login without a password, you need to transfer a copy of your SSH public key to the remote server. Therefore, you need to know your remote server’s credentials and several other details, such as hostname/IP, username, password, and port number.
To transfer the public key to the remote server, we will use the ssh-copy-id command that is available in most Linux distros. The command will copy the content of public key .ssh/id_rsa.pub to the .ssh/authorized_keys file in the remote system.
ssh-copy-id user@remote-hostCode language: CSS (css)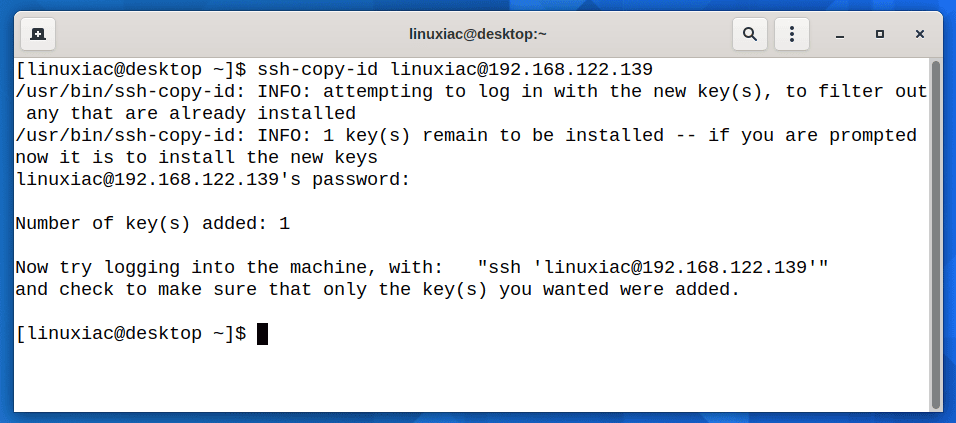
You will be prompted to enter the remote username password. Once the user is authenticated, the public key will automatically be copied into the .ssh/authorized_keys file on the remote server.
On the remote server, you can verify the transfer of the public key by viewing the content of the .ssh/authorized_keys file.
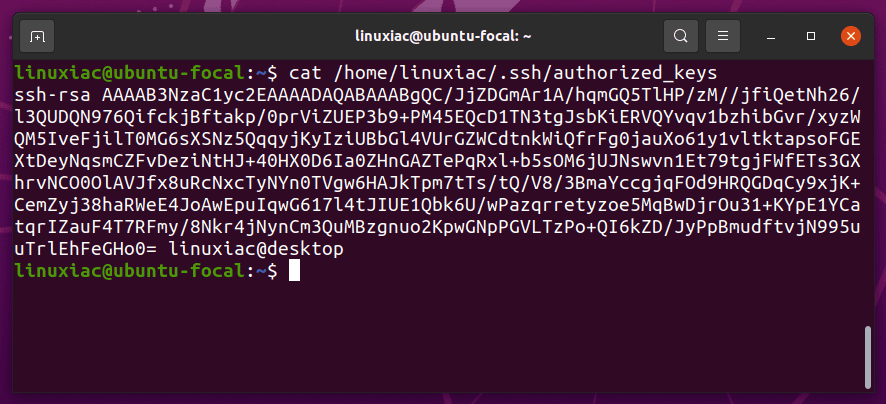
For more about the ssh-copy-id command in Linux, consult its manual page.
Step 3: SSH Login Without Password
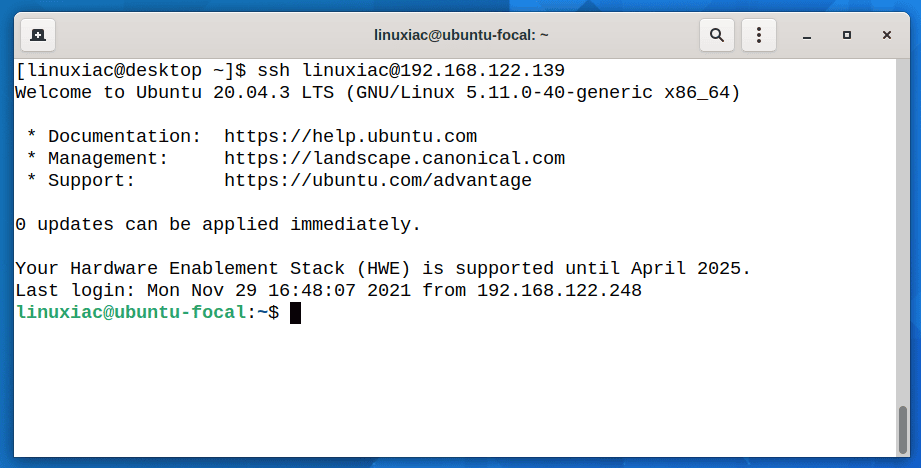
Now you should be able to login into the remote server without being prompted for a password. Just try to login into your server via SSH:
ssh username@remote_serverCode language: CSS (css)The system should log you directly to the remote server; no password is required.
Conclusion
That is all you need to set up an SSH login without passwords. Then, of course, you can add the same public key to multiple remote serves.
Finally, it’s important to note that you can share the public key (id_rsa.pub) with anyone but never share your private key (id_rsa). Only the public key is copied to the server.
The private key should never be copied to another machine because anyone with the private key will be able to log into any system having the matching public key.
If you have any questions or feedback, feel free to leave a comment.
