A new open-source tool, traur, written in Rust, has emerged for Arch users, aiming to improve security awareness in Arch Linux’s user-maintained software ecosystem by introducing automated trust scoring for AUR packages.
Traur analyzes installed or selected AUR packages and issues risk signals based on their build scripts, metadata, and past behavior. The main goal is to bring benefit to the Arch community by helping users decide how much to trust an AUR package before installing or updating it, all without running any code. And I can say that this is especially useful after several AUR packages were compromised last year.
And more detailed, Traur checks PKGBUILDs and .install scripts for risky shell commands, suspicious hooks, hidden code, and known abuse patterns. It also looks at source URLs, how checksums are used, maintainer activity, package popularity, unusual names (e.g., typosquatting), and changes in the git history that could signal risk, such as new network code or sudden changes in authors.
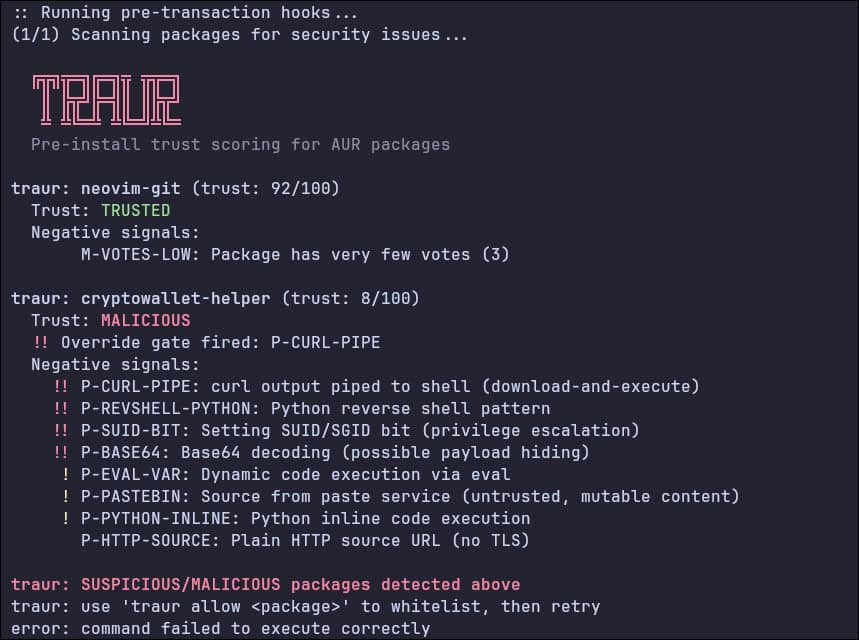
Besides static analysis, Traur uses detection methods based on real AUR malware cases, such as fake browser packages, install scripts that download and run code, orphaned package takeovers, and ways to stay hidden on a system. It looks for things like reverse shells, stealing credentials, gaining extra privileges, mining cryptocurrency, loading kernel modules, leaking environment variables, and scanning the system.
Traur’s detection uses ten separate features that give risk scores instead of just yes-or-no answers. The project says this helps highlight possibly risky packages without saying for sure if they are malware. Traur does not replace manual review or sandboxing, but it gives extra information when installing packages.
For everyday use, Traur works with popular AUR helpers like Paru and Yay through a pacman hook, showing trust scores during normal AUR installs. It can also scan all installed AUR packages, check single packages, whitelist trusted ones, or test recently changed AUR submissions at the same time.
In terms of speed, the project says Traur takes about half a millisecond to analyze each package on average. The main slowdown comes from accessing the AUR git repository.
Traur is released under the MIT license, and you can install it directly from the AUR. For more information, see the tool’s GitHub page.
For those who feel unsure about installing AUR packages, our guide “How to Install AUR Packages in Arch Linux” walks you through the process in a clear, easy-to-follow way, so you can confidently tap into this rich ecosystem of software on Arch.
Image credits: Traur

Fails to compile from AUR for me, seems unready…
Small correction: the article says traur checks install scripts for risky shell commands and known abuse patterns, but that’s not accurate. The sophisticated detection (shell analysis, GTFOBins, override gates) only runs on PKGBUILDs. Install scripts just get basic regex matching.
This matters because the July malware (librewolf-fix-bin, etc.) put their payloads in install scripts. I filed an issue on GitHub about this gap.
The other features mentioned (metadata analysis, git history, checksums) are accurate. Just don’t assume install scripts get the same level of scrutiny as PKGBUILDs.