One central part of keeping Linux servers secure is installing security updates on time. This is one of the critical tasks for Linux admins to make the system up-to-date. In addition, it keeps your system more stable and secure.
Therefore, as a system administrator, regularly updating the servers and applying security patches is one of the essential tasks to keep them stable and secure. However, if an administrator forgets it or takes this task for granted, it can lead to severe security threats.
This simple tutorial will show you to configure your Debian system to receive automatic security updates. Of course, there are many ways to automate this. However, we are going with an official method.
Install unattended-upgrades Package on Debian
Firstly, if the unattended-upgrades package is not already installed on your system, you can install it using the below commands in the console:
sudo apt update
sudo apt install unattended-upgrades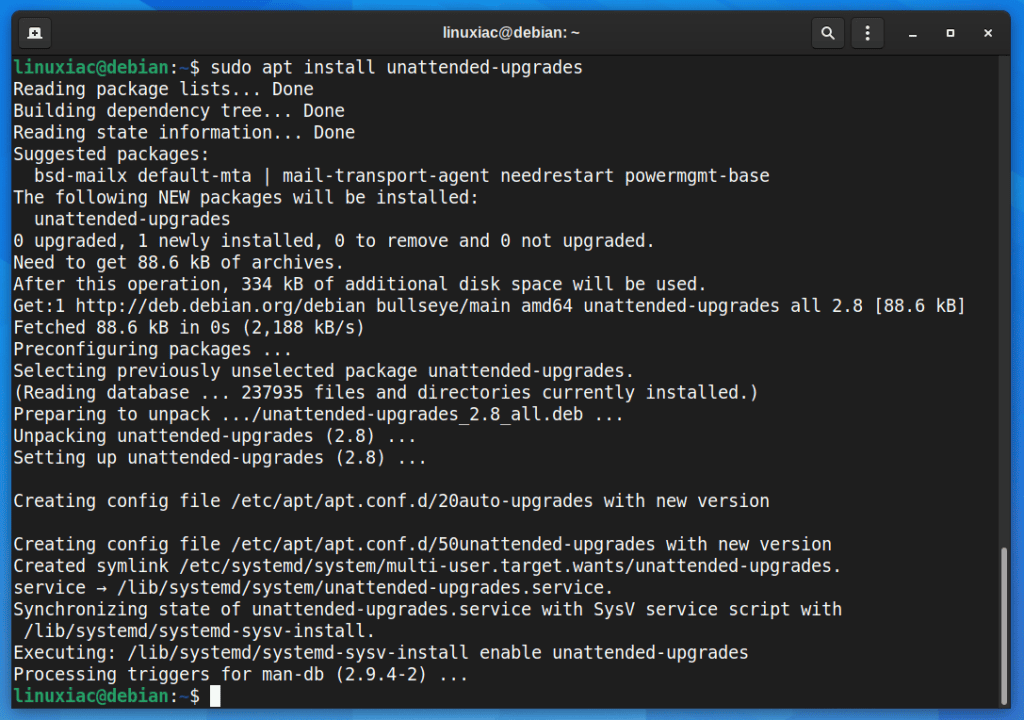
Configure Automatic Updates on Debian
The configuration file for unattended-upgrades is located at /etc/apt/apt.conf.d/ directory. Its name is 50unattended-upgrades. You can edit it using any text editor.
By default only the minimal required options were enabled for security updates. Uncomment the following lines in the file by removing // from the start of the lines:
sudo vim /etc/apt/apt.conf.d/50unattended-upgrades"origin=Debian,codename=${distro_codename}-updates";
"origin=Debian,codename=${distro_codename}-proposed-updates";
"origin=Debian,codename=${distro_codename},label=Debian";
"origin=Debian,codename=${distro_codename},label=Debian-Security";
"origin=Debian,codename=${distro_codename}-security,label=Debian-Security";Code language: JavaScript (javascript)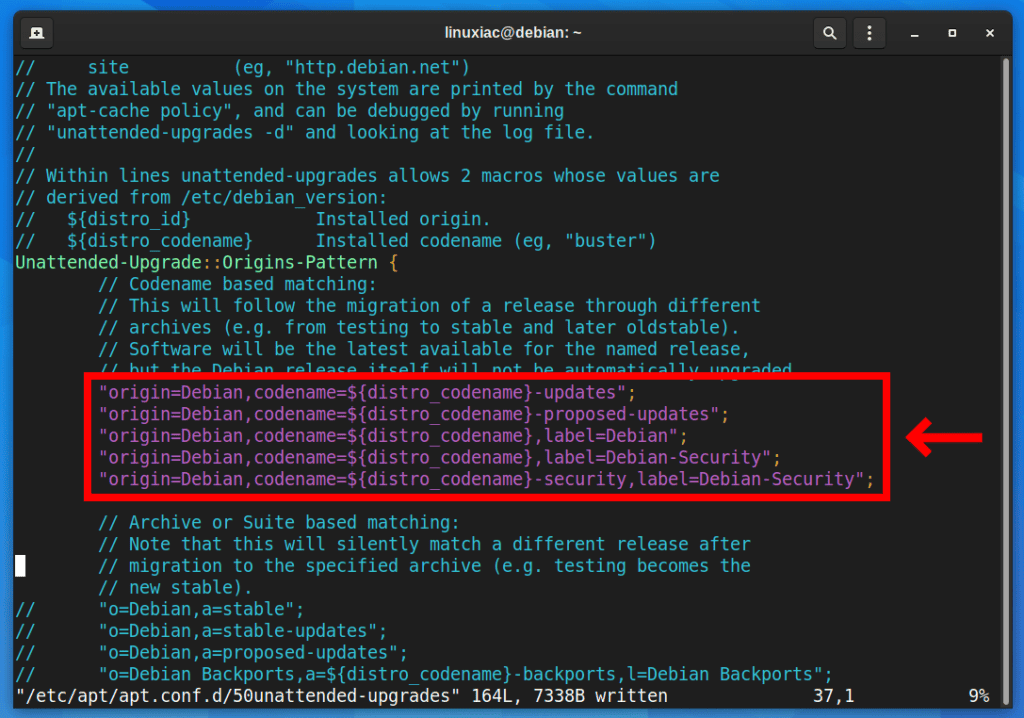
Once done, save and exit the file.
Enable Email Notification
If you like to receive email notifications from your Debian system after every automatic security update, modify the following line (uncomment it and add your email id).
Before:
//Unattended-Upgrade::Mail "";Code language: JSON / JSON with Comments (json)After:
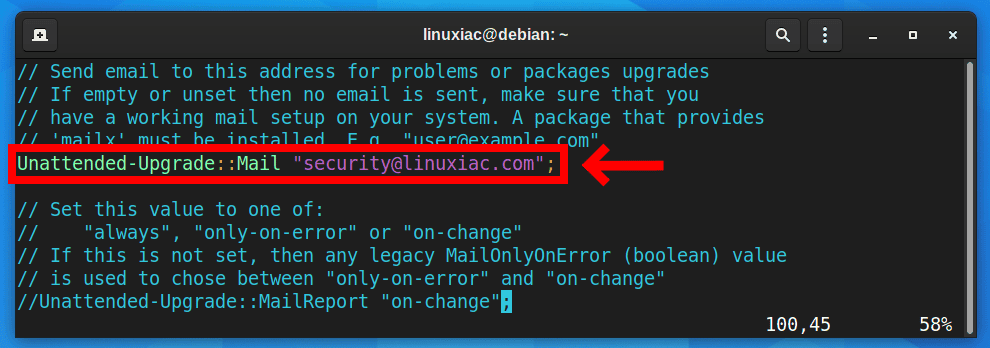
Of course, replace the email address with the current one you want to receive the notifications.
Auto Remove Unused Dependencies
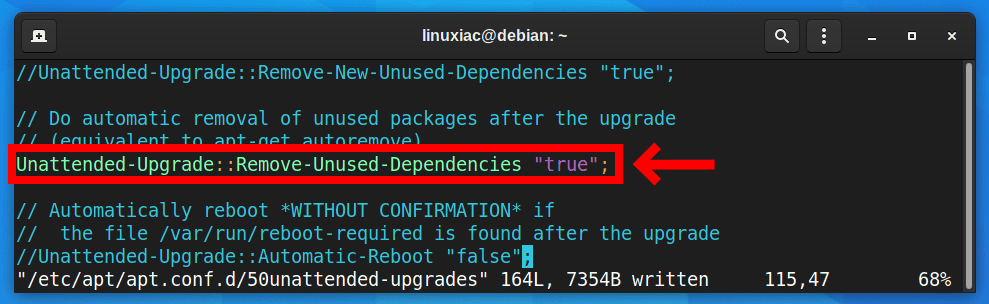
Moreover, you may need to run sudo apt autoremove command after every update to remove unused dependencies from the system. Now you can automate this task by making the changes in the following line (uncomment it and change from false to true).
Before:
//Unattended-Upgrade::Remove-Unused-Dependencies "false";Code language: JSON / JSON with Comments (json)After:
Enable Automatic Updates on Debian
To enable unattended-upgrades, you will need to configure /etc/apt/apt.conf.d/20auto-upgrades file. Issue the below command in the console to do so:
sudo dpkg-reconfigure --priority=low unattended-upgradesThe following window will appear after running the above command, automatically asking whether you want to download and install stable updates automatically. Use the tab key to select the Yes option and press Enter.
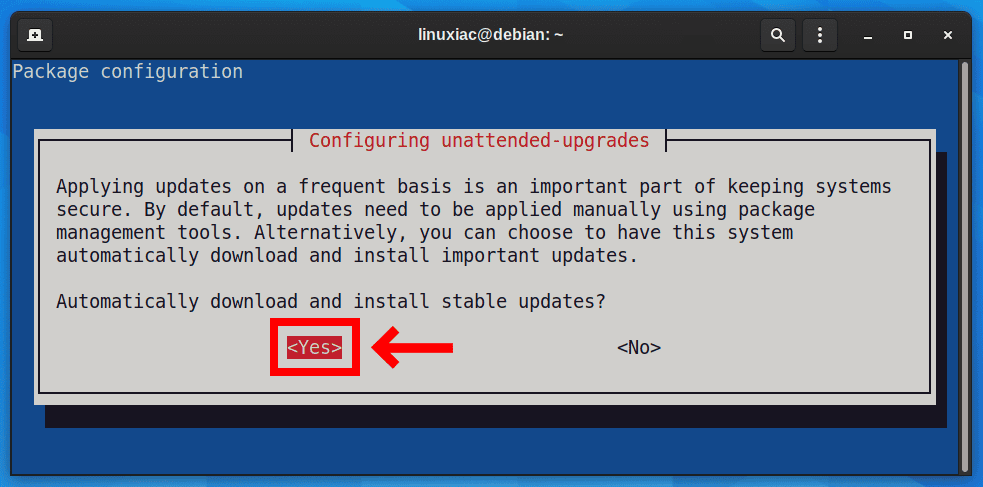
The /etc/apt/apt.conf.d/20auto-upgrades file will be updated with the following content:
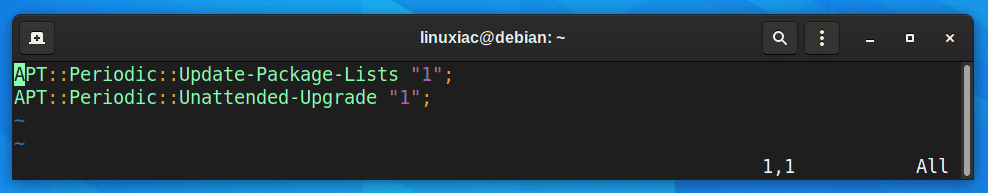
To view whether the unattended-upgrades service is enabled and running, you can issue the command shown below:
sudo systemctl status unattended-upgrades.serviceCode language: CSS (css)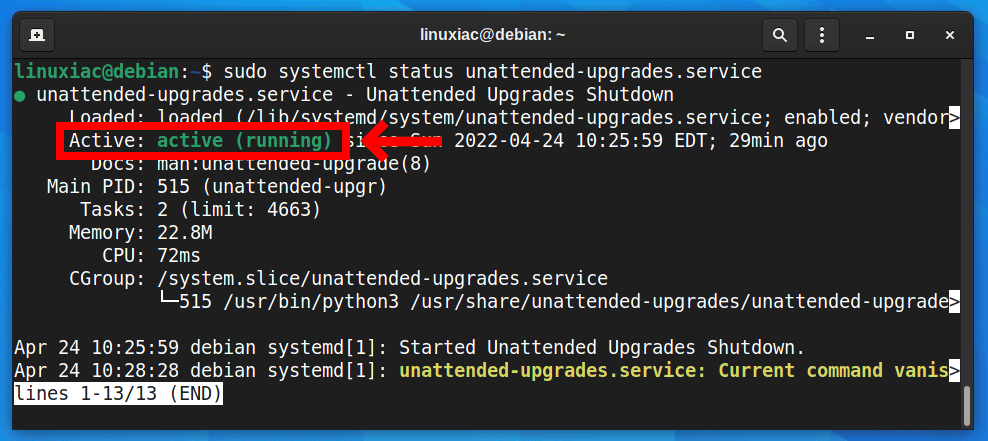
As you can see from the output, the unattended-upgrades service is enabled to install updates automatically.
If the service is not allowed and started, you can do so by typing:
sudo systemctl enable unattended-upgrades
sudo systemctl start unattended-upgradesWhen the system performs the unattended upgrade, it logs this activity in the files under /var/log/unattended-upgrades/ directory.
Disable Automatic Updates on Debian
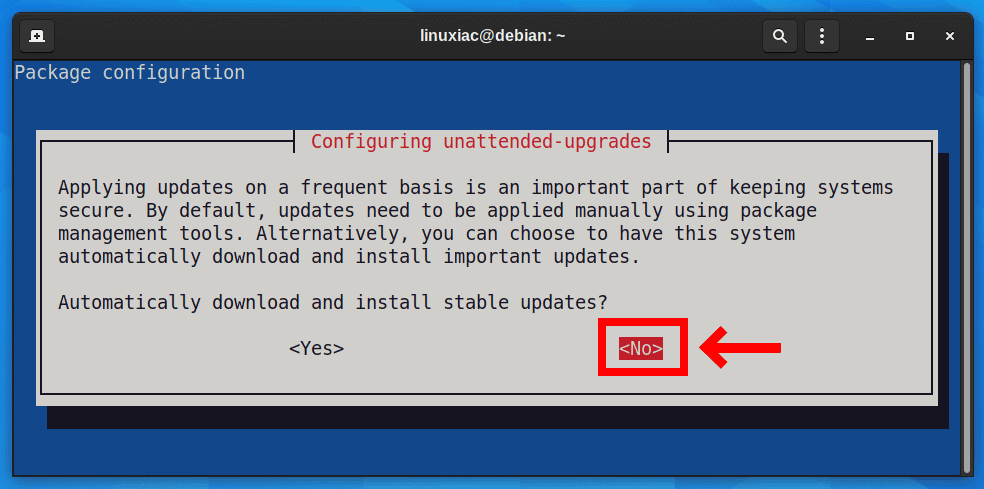
To disable the unattended upgrades, issue the command shown below:
sudo dpkg-reconfigure --priority=low unattended-upgradesThe following window will appear, asking whether you want to download and install stable updates automatically. Use the tab key to select the No option and press Enter.
Conclusion
By enabling the automatic updates on Debian servers, you’ve taken an important step to protect your server from vulnerabilities.
Manually updating the system and applying patches can be a very time-consuming process. So the unattended-upgrades save a lot of time.
The unattended-upgrades utility keeps your system current and secure by automatically installing the latest updates and security patches whenever they are available.

Yeah, you'd have to configure your local MTA for that.
I am not getting any emails with the “Unattended-Upgrade::Mail “”;” set to my email address
Hi,
thanks for the well written post, helped tremendously.
Kind regards,
bene
Hi Bene,
I’m glad to be of service. 🙂
Best,
Bobby