Password authentication is the default method most SSH clients use to authenticate with remote servers. Still, there’s one big drawback: they are exposed to potential security vulnerabilities, such as brute-force login attempts.
To address this, a more secure alternative is to use SSH key-based authentication, which involves generating an SSH key pair and storing it on your computer. This approach provides strong, passwordless authentication that’s both more secure and more convenient than using traditional passwords.
The central concept is that instead of a password, one uses a key file that is virtually impossible to guess. Here’s what happens:
- You create two keys — a private key (kept secret on your computer) and a public key (placed on the server).
- When you connect, the server checks that your private key matches the public key it knows.
- If they match, you’re granted access — no password needed.
With that said, let me show you how to create such an SSH key pair. As you’ll see, it’s a straightforward process.
How to Generate an SSH Key Pair on Linux
When generating SSH keys, you need the ssh-keygen command, which is part of the SSH suite and used to create new authentication key pairs. However, there’s one important thing you need to figure out before generating the keys—what type (algorithm) they should be. Here are the most commonly used options.
- DSA: Very old and now deprecated. Limited to 1024-bit keys, which are no longer considered secure. Avoid using it!
- RSA: Oldest and most common SSH key type. Widely supported everywhere, even on older systems. Security depends on key length — use at least 4096 bits today.
- ED25519: Modern and highly secure key type using elliptic-curve cryptography. Much faster and shorter than RSA while being equally (or more) secure. Harder to crack and resistant to certain types of attacks.
That said, I’d strongly recommend going with ED25519—it’s the most reliable and well-established option today. So, open up the terminal and run the following command:
ssh-keygen -t ed25519 -C "your_email@example.com"Code language: Bash (bash)While the -C option is optional, it adds a helpful comment — usually your email — to help identify the key. With -t ed25519, you’re being explicit, telling SSH which exact algorithm to use. On modern systems (OpenSSH ≥ 7.8), it’s the default.
You’ll be asked to enter a passphrase—keep hitting “Enter“. The command generates a pair of keys in the ~/.ssh directory by default.
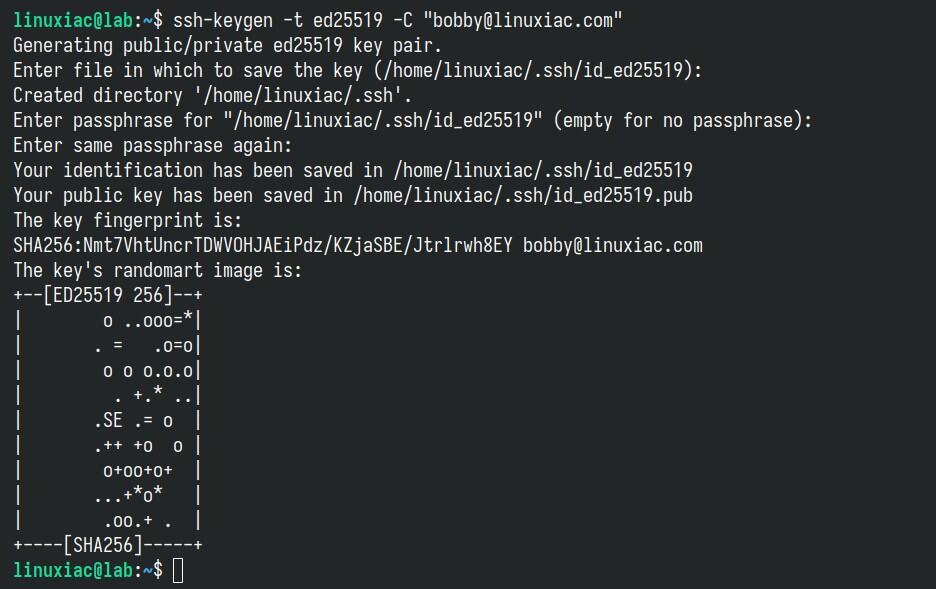
You now have two files:
id_ed25519(private key). The private key is stored on your local computer and should be kept secure, with permissions set so that no other users on your computer can read the file.id_ed25519.pub(public key). The public key needs to be placed on the server you intend to log in to. You can freely share your public key with others.
ls -la ~/.ssh/Code language: Bash (bash)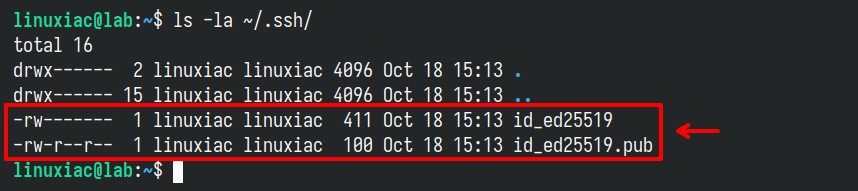
~/.ssh directory.Now, you can place the public key on any server (in the .ssh/authorized_keys file) and then connect to it using SSH. When the public and private keys match, the SSH server grants access without a password.
However, if you are unsure how to do it, fear not. Just take a look at our short and easy-to-follow guide, “How to Set Up SSH Login Without a Password,” where everything is explained.
Finally, if for some reason you have decided to stick with the RSA type, ensure you generate the keys with the -b 4096 option. This instructs ssh-keygen to increase the number of bits used to create the key pair, which is recommended for increased security.
ssh-keygen -t rsa -b 4096Code language: Bash (bash)Conclusion
In this article, you have learned how to generate SSH key pairs using ssh-keygen. SSH keys have numerous advantages over passwords, with the main ones being:
- Increased security: They are nearly impossible to brute force or guess.
- Ease of management: No more creating and changing random passwords.
- Automated tasks: Because you don’t need to type your password every time, it’s easier to automate tasks that require SSH.
For more about the ssh-keygen command in Linux, consult its manual page. As always, feel free to leave a comment if you have any questions.

Thank you both. To Steve, for the proper remark, and to Ricardo, for the good answer.
I will soon publish an article related to SSH passwordless login.
“You can place the public key on any server, …” Please expalain how one can place the public key on the server.
You can use ssh-copy-id, e.g.:
ssh-copy-id -i ~/.ssh/id_rsa.pub user@server
Or manually by copying the contents of ~/.ssh/id_rsa.pub into the user’s ~/.ssh/authorized_keys file on the server.
If you do it manually, make sure to put permissions 0700 for ~/.ssh.
Cheers.