Cloudflare released OPKSSH (OpenPubkey SSH) as open source (Apache-2.0 license) under the umbrella of the OpenPubkey project. And let me tell you, this is big because this move brings single sign-on (SSO) to SSH without requiring any changes to the standard SSH protocols or software.
Previously owned by BastionZero (later acquired by Cloudflare), the code has now been donated to the OpenPubkey community for broader adoption and community-driven enhancements.
As you know, SSH has long stood as a cornerstone of secure administration, yet it has also introduced complexities around managing SSH keys.
Many organizations struggle with an abundance of outdated authorized keys that remain on servers indefinitely, even when employees leave or their roles change. OPKSSH is now here to change this.
At the heart of OPKSSH is its ability to leverage single sign-on with OpenID Connect. Essentially, instead of generating and maintaining your own SSH key pairs for every server you access, you can rely on ephemeral key pairs that self-destruct once they are no longer needed.
This removes the hassle of handling long-lived keys, reduces the risk of compromise, and shrinks the exposure window if a private key is ever stolen.
How OPKSSH Works?
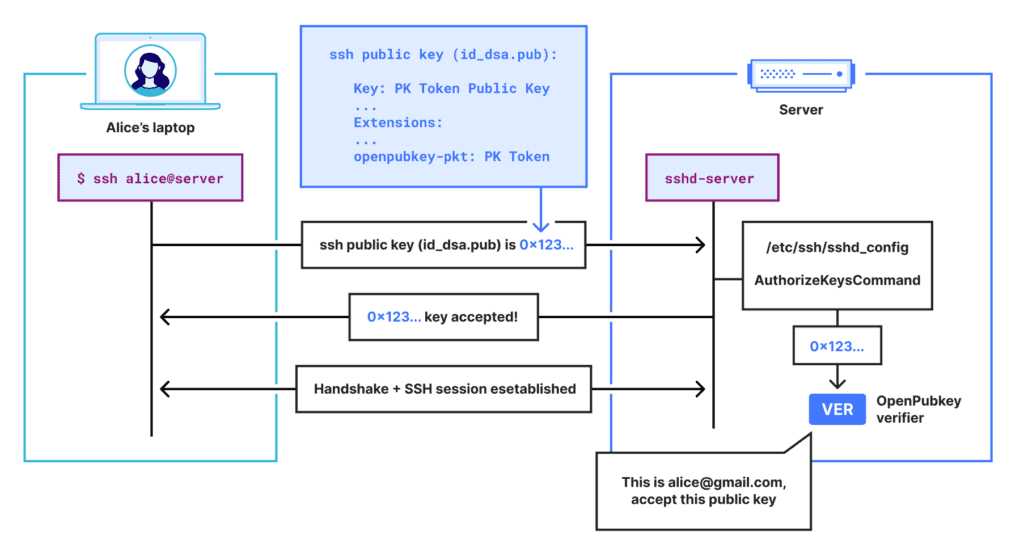
OpenPubkey is a project that effectively embeds a user’s public key within standard ID Tokens, transforming these tokens into “PK Tokens.” This approach preserves compatibility with existing single sign-on workflows and identity providers like Google, Azure, or Okta.
Consequently, administrators and users benefit from stronger security while relying on established identity platforms they already trust.
OPKSSH takes the idea a step further by enabling these PK Tokens to function within SSH. Thanks to this integration, when a user signs in via their identity provider, OPKSSH automatically generates a short-lived public/private key pair and stores the public key as a certificate-like structure.
The SSH server, configured to call an OpenPubkey verifier, simply needs to confirm that the provided token is valid, unexpired, and signed by the correct identity provider. This removes the age-old manual step of distributing user keys for every server across an organization.
Under normal circumstances, SSH requires a client to present a public key whose corresponding private key is stashed locally. Administrators must then list this public key in the server’s authorized_keys.
OPKSSH does away with that entirely by injecting an ephemeral key and PK Token into an SSH certificate extension, which gets sent to the server as part of the usual SSH handshake.
On the server side, an extra line in sshd_config designates a custom AuthorizedKeysCommand pointing to the OpenPubkey verifier. This script checks if the token is still valid, makes sure the user’s ephemeral public key matches the key in the token, and determines whether the user’s email address is approved for access.
Check the official OPKSSH’s README in its GitHub repository for a closer look at the installation steps or to try them out yourself. The Clodflare’s announcement is here.

Nice!
At $DAYJOB we’re replacing SSH keys with certificates integrating Smallstep’s step-ca, which also integrates with our OIDC platform.But I’m going to take a look at this project, thanks for posting about it!