Microsoft kicked off a new open-source project (MIT-licensed) called LiteBox that explores a different approach to application isolation by using a sandbox-focused library operating system rather than a full traditional OS.
Written in Rust, LiteBox is host-agnostic and built to run code on a deliberately minimal, security-focused operating system surface. The main idea is that instead of exposing applications to the wide range of system calls, kernel subsystems, and services, it provides a narrowly scoped interface tailored to the workload being executed.
The aim is to reduce the attack surface and limit the blast radius of vulnerabilities in both applications and the host system.
The project follows the library OS model, where core operating system functionality is packaged as libraries that accompany the application. In this design, the application provides its own constrained OS environment, reducing dependence on a large host kernel.
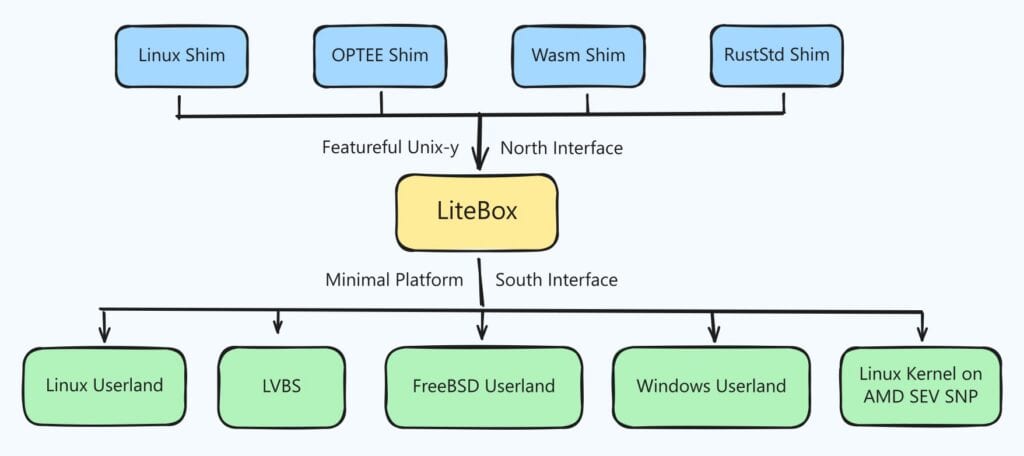
Regarding possible use cases, on Linux, for example, LiteBox can be used to sandbox Linux workloads while exposing significantly less of the kernel than containers typically do.
On Windows and other supported platforms, it provides a Linux-like execution environment without requiring a full Linux kernel, enabling unmodified Linux programs to run on Windows hosts without a full Linux virtual machine.
Moreover, it can operate on top of confidential computing technologies such as AMD SEV-SNP, leveraging hardware-encrypted memory and reducing reliance on the host. In addition, LiteBox can host OP-TEE programs on Linux, providing a minimal OS environment for trusted execution workloads.
Target use cases also include sandboxing untrusted or semi-trusted code, executing user-supplied workloads in cloud services, running CI jobs, and supporting confidential computing deployments where minimizing the trusted computing base is critical.
Finally, it’s important to understand that the project is not intended to replace Linux, Windows, or existing container technologies, nor is it for desktop or general-purpose use. Instead, it serves as a focused execution layer for tightly controlled workloads that require predictable behavior and reduced OS exposure.
At the moment, LiteBox is still in an early, experimental phase, so there are no stable releases yet. However, the project looks very promising, and we’ll be following its development with great interest.
For more information, visit the project’s GitHub page.
Image credits: LiteBox Project

Micropof & security lol ya shure. Typical american garbage.