As we informed you last Friday, Arch users experienced difficulties accessing some services. Yesterday, the distribution shared an official statement about it.
In it, the Arch Linux Project has confirmed that recent outages affecting its infrastructure are the result of an ongoing DoS attack. The disruptions have primarily hit the project’s main website, the Arch User Repository (AUR), and its community forums.
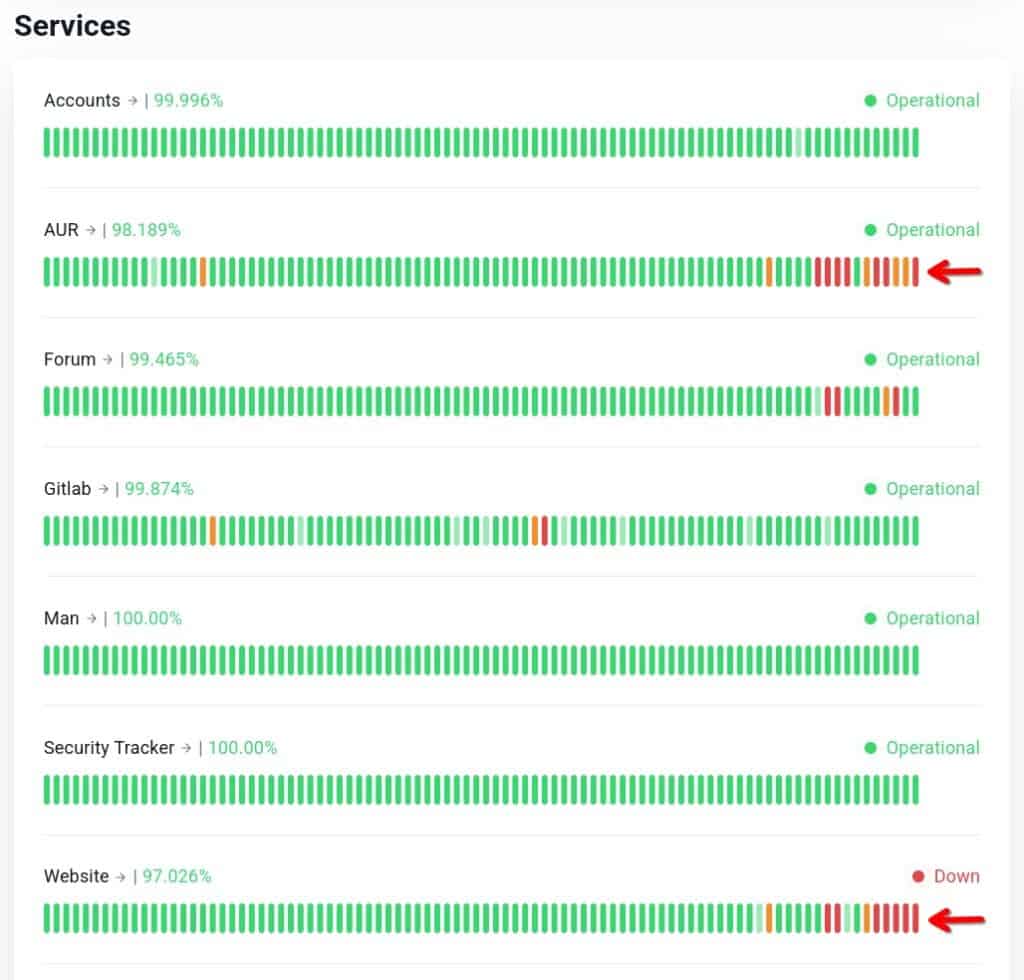
Developers said they are working closely with their hosting provider to mitigate the attack while also weighing longer-term options, including dedicated DDoS protection services.
The Arch Linux Project is currently experiencing an ongoing denial of service attack that primarily impacts our main webpage, the Arch User Repository (AUR), and the Forums. We are aware of the problems that this creates for our end users and will continue to actively work with our hosting provider to mitigate the attack.
To help keep users in the loop, Arch has committed to posting regular updates on its service status page. In the meantime, workarounds are available. If the main archlinux.org site is unavailable, tools like reflector—which normally pull updated mirrors from the official endpoint—won’t work. In that case, users should fall back on the mirrors already listed in the pacman-mirrorlist package.
Users are also reminded always to verify the integrity of these downloads with trusted signatures.
For AUR disruptions, the team maintains a GitHub mirror where packages can be retrieved directly via Git. This option provides some continuity for users who rely on AUR packages during the ongoing attack.
Arch also noted that some services may appear unresponsive on the first attempt because of TCP SYN authentication checks from the hosting provider. In most cases, retrying the request allows connections to succeed.
Lastly, the developers explicitly declined to share technical details about the attack or its origin, citing security concerns. Once the issue is fully resolved, those details will probably be shared with the public.

The Linux Mint Forum and Blog have also been the victim of such an attack in recent days… An entity that has not yet been officially identified is after Linux ;-(
they need to use a dedicated DDoS protection service like cloudflare so we can be done with this issue
That wouldn’t work lol, the AUR works by leaving the door open so you can swiftly install and update your packages. Introducing cloudflare would cause discomfort, as you’d have to do a captcha in the terminal lol. Anyways, the AUR is a completely unexpected DDoS victim, I’m guessing someone has a discreet malicious intent, not the usual mess around war support.
I take it you’ve not ever actually deployed Cloudflare’s WAF, because Turnstile isn’t the only solution for mitigation. I only use it for login forms, because that’s where its use makes sense. For unwanted traffic, I sinkhole it before it even has the opportunity to be presented with a Captcha. Why would you want it to even get that far? 🙂
They’re intentionally choosing not to do so as cloudflare is not open source.